Table of contents
Introduction
In the current digital Environment, safeguarding your infrastructure against potential attackers is a critical priority. As cyber threats continue to evolve, implementing robust security measures becomes indispensable. This blog presents a comprehensive approach to securing your infrastructure using penetration testing and vulnerability scanning, supported by a range of open-source tools. Let’s delve into the best practices and steps you can take to defend your digital assets.
Vulnerability Scanning: A Crucial First Step
1. Understanding Vulnerability Scanning
Vulnerability scanning is the initial step towards identifying weaknesses within your system. It involves assessing if your systems are up to date and properly configured according to established documentation.
2. Importance and Benefits
Vulnerability scanning provides invaluable insights into potential system weaknesses and misconfigurations. By pinpointing these vulnerabilities, you can take corrective actions to enhance overall security. This practice is not just recommended – it’s necessary to ensure your infrastructure’s resilience against potential attacks.
Exploring Open Source Vulnerability Scanning Tools
1. OSV-Scanner
osv-scanner is a dependency scanner tool designed to detect outdated and vulnerable packages of apps (node.js,react.js etc..).
Prerequisites:
Ubuntu 22 or later version required and golang latest version
How to Run:
# Install golang sudo add-apt-repository ppa:longsleep/golang-backports sudo apt update sudo apt install golang # Install osv-scanner go install github.com/google/osv-scanner/cmd/osv-scanner@v1 # Scan for vulnerable dependencies sudo ~/go/bin/osv-scanner -r /path/to/yourapp/
Output:
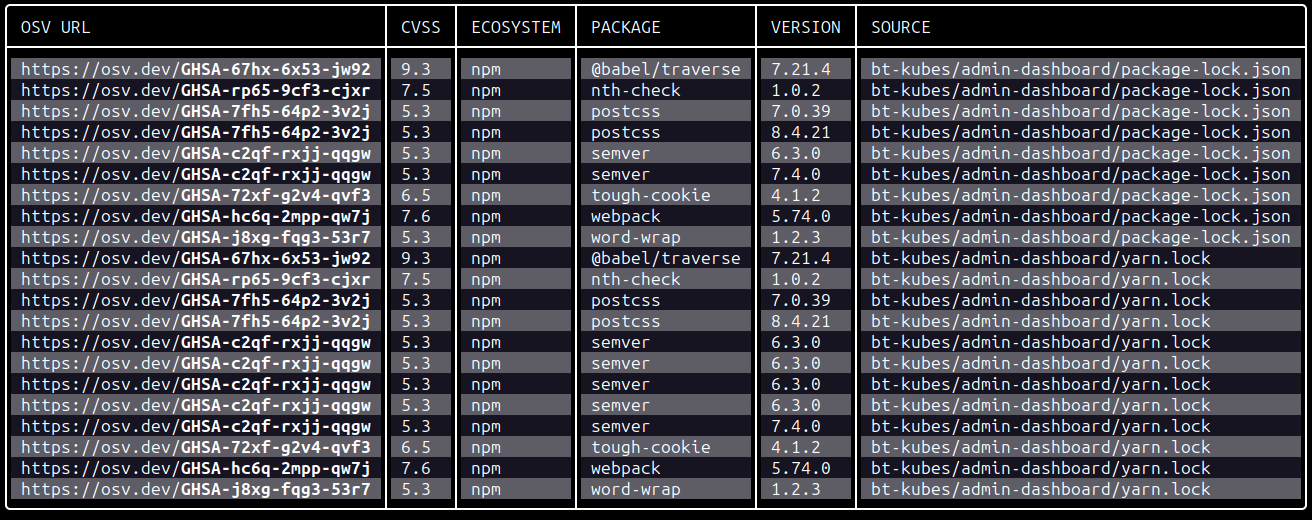
2. Wapiti
Wapiti is a tool for scanning URLs and databases for vulnerabilities, generating comprehensive reports.
Prerequisites:
Ubuntu 22 or later version required
How to Run:
# Install wapiti sudo apt install wapiti # Run wapiti scanner wapiti -u <URL>
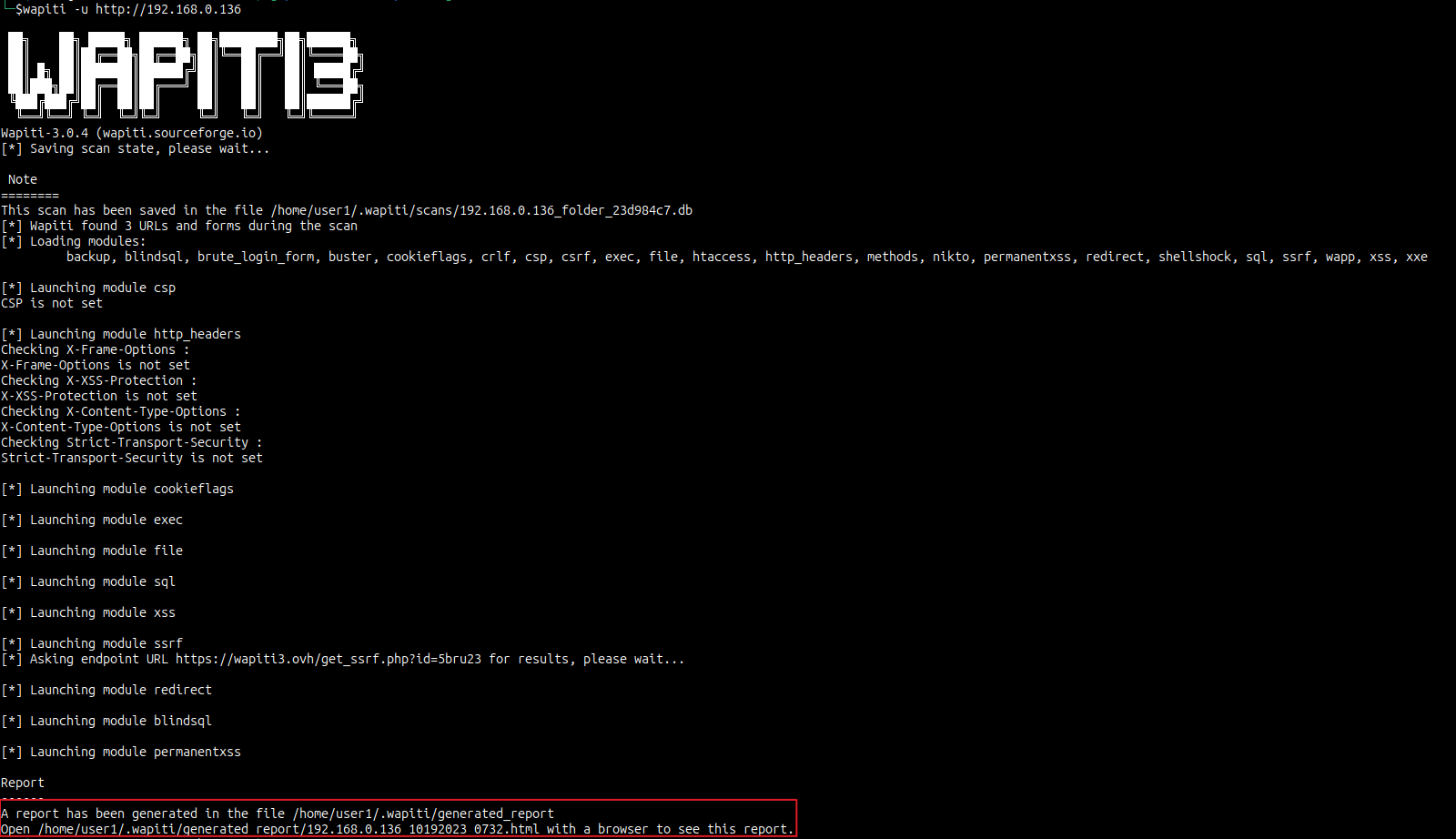
Output:
From the below output, You should have received a similar location of where the result is stored.
3. OWASP ZAP
OWASP ZAP is an advanced tool for uncovering vulnerabilities through website penetration testing, providing detailed reports and solutions.
Prerequisites:
JRE 11 or above, python3-pip
How to Run:
Option 1 : Using Command line Interface
Download and Install OWASP ZAP: To download and install OWASP ZAP from the official website:
· Click the below link https://www.zaproxy.org/download/
· Click download button from the Linux package
Extract it and open a terminal window
Launch OWASP ZAP in Daemon Mode: To use OWASP ZAP in the CLI, you can start it in daemon mode, which allows you to control it via the command line. Then, execute the following command to Install zap-cli using pip,
pip install --upgrade zapcli --break-system-packages zap.sh -daemon -host 127.0.0.1 -port 8080 -config api.disablekey=true
Note: –break-system-packages will either update dependencies or downgrade them as needed, please make sure to take note of any changes.
Open another terminal in the same folder and type the following commands to start scanning your web application.
zap-cli -p 8080 spider <target_url>
Note : If you are running a Node/React application, it is recommended to run Ajax spider method.
zap-cli -p 8080 ajax-spider <target_url>
Zap cli will start scanning your web application to produce results enter the following command,
zap-cli -p 8080 report -o <output_filename> -f json
For the output we can specify the html format, enter the following command
zap-cli -p 8080 report -o <output_filename> -f html
Option 2 : Using Desktop UI Environment
Download and install from the official website
https://www.zaproxy.org/download/
After the Download completes, navigate to the Downloads folder in a terminal window.
Here use ‘ls’ command to make sure the downloaded file is there
Now enter the following command
# Make sure the filename match sudo chmod +x <filename>.sh
Now execute it in the terminal,
sudo bash <filename>.sh
An installation wizard will open up
Click next,
Click I accept the agreement and click next,
Here custom installation will let you install the app in a separate directory if you want.
Otherwise click next and next again It will start installing
Click finish you have successfully installed ZAP
Now open the application ‘OWASP ZAP’
If you want, you can persist the current session and click start
Click on the automated scan,
Enter the appropriate URL and check the option Use ajax spider for more accurate results and also it is recommended to use chrome headless in the drop down list.
Click on the attack button and the ZAP will start scanning your app. After the scan is done, the results will be displayed in the ‘Alerts tab’ ,
Also Utilize features like active scans, passive scans, AJAX spider attack, etc.
Conclusion
In conclusion, bolstering your cybersecurity defenses through a comprehensive strategy that includes Vulnerabilities App scanning and penetration testing using open-source tools is paramount. By diligently identifying weaknesses and taking proactive measures, you can fortify your digital assets, ensuring robust protection against potential threats. Your commitment to vigilance and best practices is the key to securing your infrastructure in an ever-evolving digital landscape.